It’s a well-known joke that the S in IoT stands for security. It’s also a well-accepted fact that we cannot make that joke about connected vehicles. In this blog post we discuss some cybersecurity aspects of the connected vehicle solution. As the topic is really broad, we focus on examples from the security work done for the solution, as well as the new possibilities introduced by the solution.
What is Security?
Security is the protection of assets
With connected vehicle solutions, these assets include data, privacy and control, among others. Want a more concrete example? A compromise of control can lead to unwanted behavior of the vehicle. This can take many forms, from breaking into a vehicle by utilizing remote control APIs to open car doors to ransomware blocking your usage of the whole vehicle.
The approach for protecting assets in the connected vehicle solution consists of three base assumptions:
- Any complex system will inevitably contain vulnerabilities.
- Some vulnerabilities will inevitably be discovered.
- Discovered vulnerabilities will inevitably be exploited.
Flipped around, the base assumptions can be used to derive the three base layers of protection required to secure a connected vehicle solution:
- Hacking protection, which makes vulnerabilities hard to find and exploit.
- Hacking mitigation, which detects hacking attempts, logs security incidents and even adjusts security in real time.
- Data protection, which prevents exposure and ensures privacy of data in the event of uncontrolled attacks.
Security Processes
Security processes range from operational processes based on international standards, such as the ISO 27000 series, to design methodologies, such as the threat and risk assessment (TARA), and implementation practices, such as the CERT Secure Coding Standard. Operational processes are the underlying foundation that guarantee the integrity of the systems, in which the connected vehicle solution is designed, coded, manufactured and operated.
The cloud platform, based on Microsoft Azure, has more certifications than any other cloud provider, including the most important operational standards. The production facilities for the Motion T in-vehicle platform are ISO 27000 certified, as are the operational facilities run by Irdeto.
Security by Design
Design time security begins with the threat and risk analysis (TARA). TARA will define the objectives of attackers (threats) and the likelihood of them reaching their objectives (risks). Following is an actual example from the TARA of the in-vehicle platform, Motion T. What does a TARA contain then? Here is an excerpt of an actually very long table of contents of a TARA:

All the various actual routes attackers can utilize to reach their objectives in a particular system are defined in attack trees. For a complex system like the LM carputer, the attack trees will can become incredibly complicated. For a concrete example, this is just a small sub-tree from the full attack-tree of the Link Motion carputer:
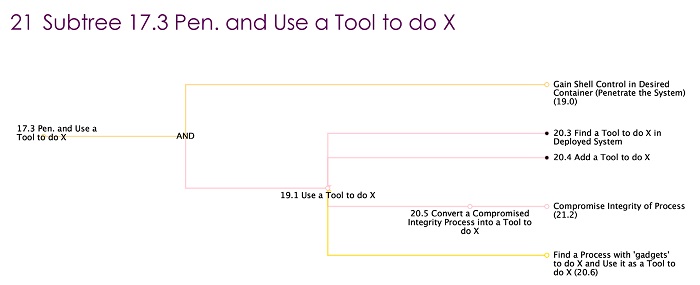
Once the attack trees have been identified, mitigations need to be established to impede various branches of the attack tree. Mitigations can be established at one or multiple points for attack trees, and it’s crucial to identify steps that repeat across multiple different attack paths. So, what would a mitigation for a specific attack look like? Here’s an example:
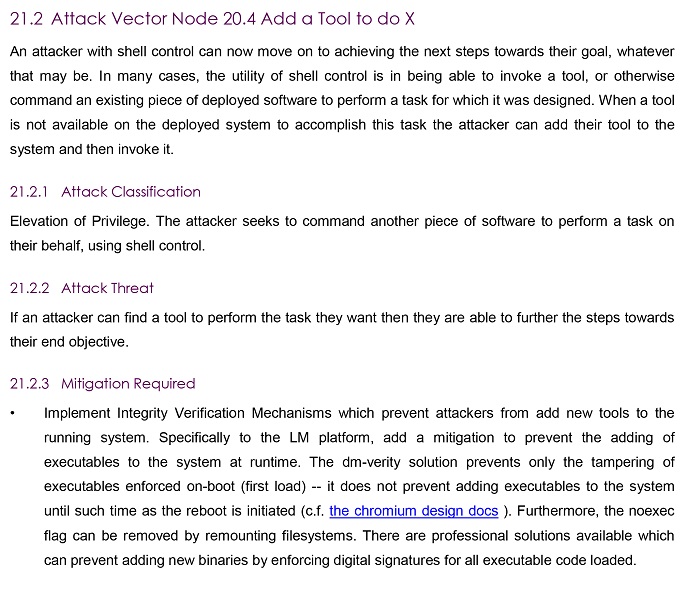
Mitigations are validated and verified using a plethora of methodologies and technologies. As non-comprehensive examples, Irdeto performs security reviews on Link Motion’s architecture and we at Link Motion run static code analyses against certain secure coding rule sets.
Post Production Security
Cybersecurity-wise, the key technologies of the connected vehicle solution are live telemetry and over-the-air updates, which greatly enhance the possibility for hacking mitigation and deployment of new hacking protections.
There are three major flavours to this:
- Hacking attempts can be detected in real time by analysing data received from cybersecurity monitors deployed on the in-vehicle platform in vehicles.
- Temporary hacking mitigations or data protections, even erasure of sensitive data, can be deployed instantly using over-the-air updates, while permanent hacking protection is developed.
- New hacking protections can be deployed continuously, in response to both detected and exploited vulnerabilities.
Epilogue
A stark reminder of the crucial nature of all of the topics discussed here was just delivered recently by the US Government Accountability Office (GAO). As reported by the BBC, the GAO report details mission critical cyber-vulnerabilities in nearly all cutting-edge weapons systems tested between 2012 and 2017. The exact kind of vulnerabilities, that we cannot accept in connected vehicles. Especially important is the need for SW hardening as an integral part of the development process every step of the way, even after product deployment through Over-The-Air (OTA) updates.
Security should never be an afterthought, nor can it be bolted on after the fact.

-
Juha Hytönen
juha.hytonen@link-motion.com
Head of Quality and Compliance
Link Motion

-
Antti Korventausta
antti.korventausta@link-motion.com
Lead System Architect
Link Motion